We learn how smart contracts written in solidity are deployed, and how it can be used to backdoor a contract.
I thought I know Ethereum smart contract security, but this challenge punched me in the face. This video goes over a basic first code review to understand the contract setup.
I thought I know Ethereum smart contract security, but this challenge punched me in the face. This video goes over a basic first code review to understand the contract setup.
In this video we identify a backdoor and find the gadgets to do Jump-oriented Programming in a ethereum smart contract
In this video we identify a backdoor and find the gadgets to do Jump-oriented Programming in a ethereum smart contract.
In this video we identify a backdoor and find the gadgets to do Jump-oriented Programming in a ethereum smart contract.
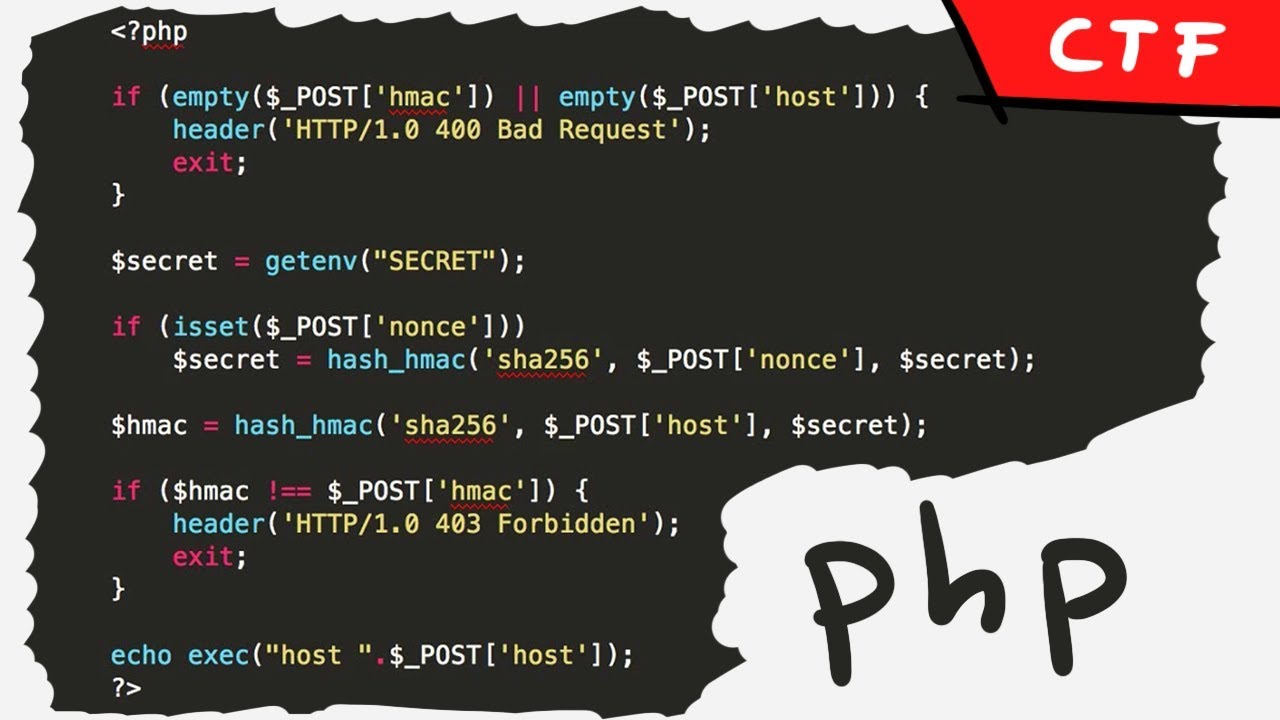
This short php code contains a critical vulnerability. In this video I will explain in detail what I think while analysing it.
This short php code contains a critical vulnerability. In this video I will explain in detail what I think while analysing it.
This challenge was an amazing team effort. The final stage was a bash eval injection, but without using any letters or numbers.
This challenge was an amazing team effort. The final stage was a bash eval injection, but without using any letters or numbers.
At first I was not able to solve the mindreader challenge, even though it was supposed to be easy. I have a critical look at my approach and figured out two major mistakes I made.
At first I was not able to solve the mindreader challenge, even though it was supposed to be easy. I have a critical look at my approach and figured out two major mistakes I made.
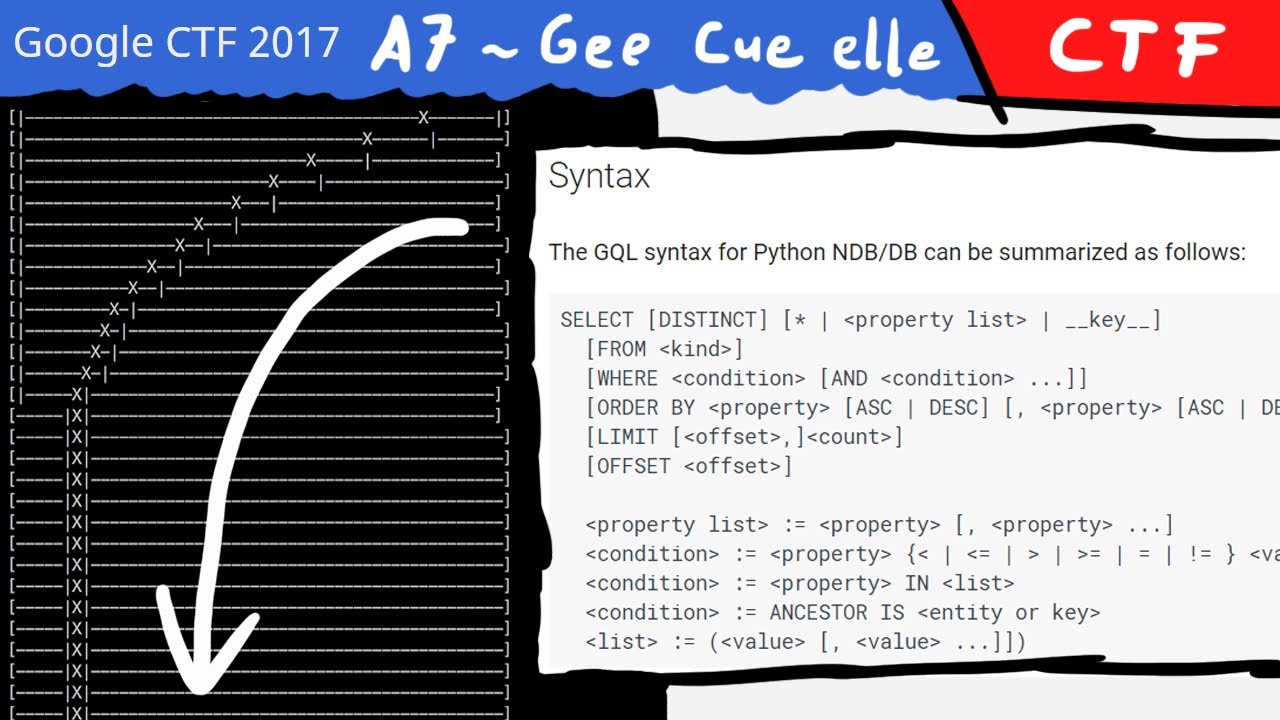
After finding and analysing the source code we found a GQL injection. Unfortunately there is a system in place that will ban you for too many requests. So we use a modified binary search algorithm to finish in time.
This was considered a hard challenge. After finding and analysing the source code we found a GQL injection. Unfortunately there is a system in place that will ban you for too many requests. So we use a modified binary search algorithm to finish in time.
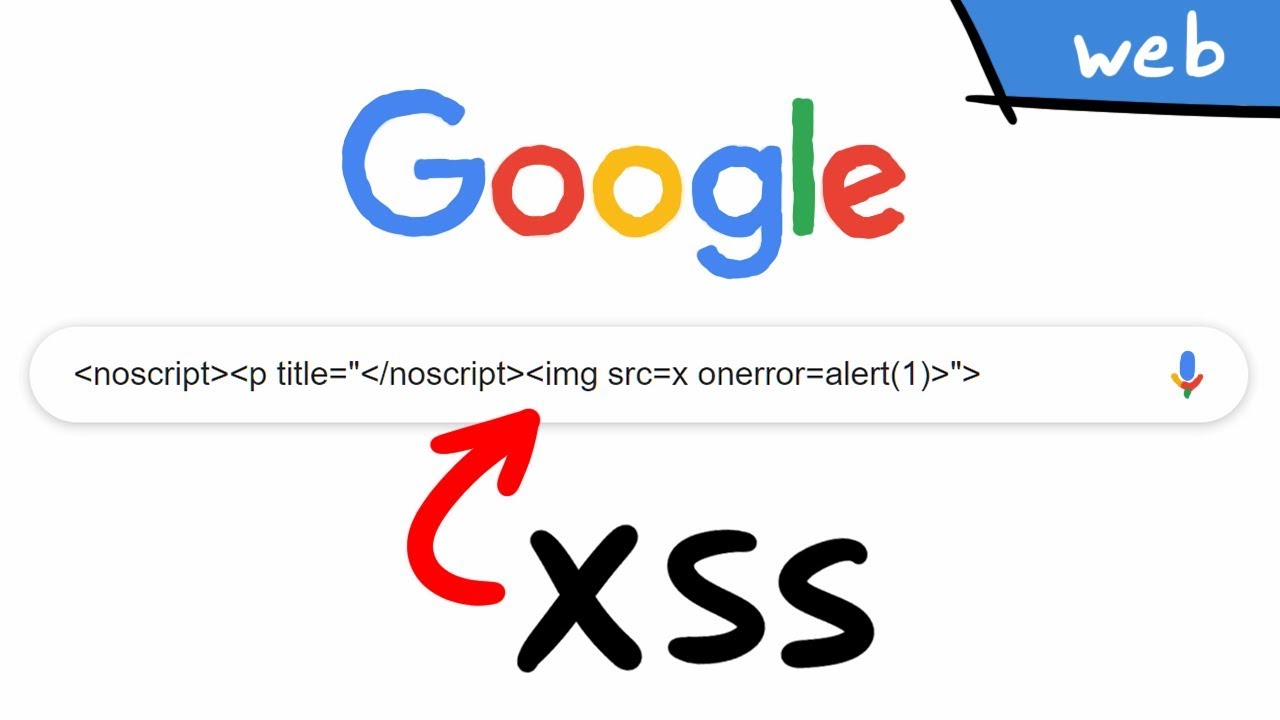
An actual XSS on google.com by Masato Kinugawa. It abuses a parser differential between a JavaScript enabled and disabled context.
An actual XSS on google.com by Masato Kinugawa. It abuses a parser differential between a JavaScript enabled and disabled context.
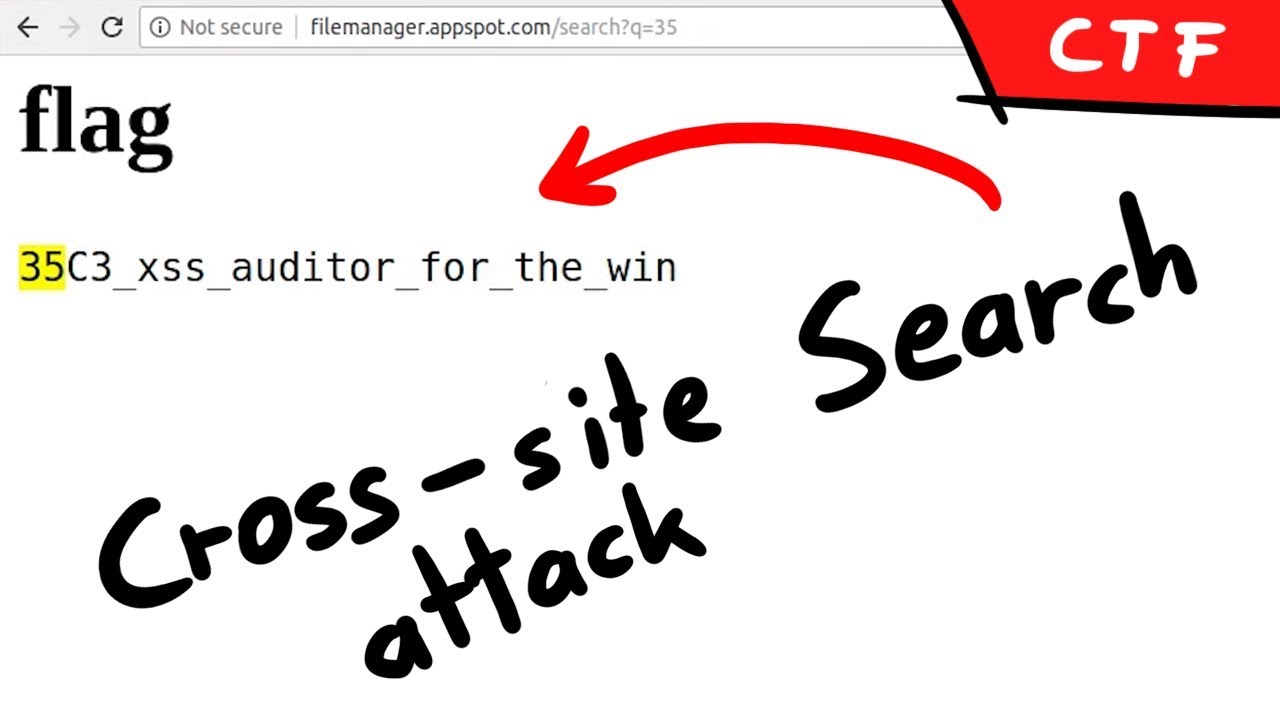
Leaking data through a search cross origin, by abusing a behaviour of Chrome regarding iframed pages that trigger errors.
Leaking data through a search cross origin, by abusing a behaviour of Chrome regarding iframed pages that trigger errors.
Hacking Competition in China. Our team qualified for the Real World CTF finals in China organised by Chaitin Tech, which was a really awesome CTF. In this video I want to share my experience and thoughts about the event.
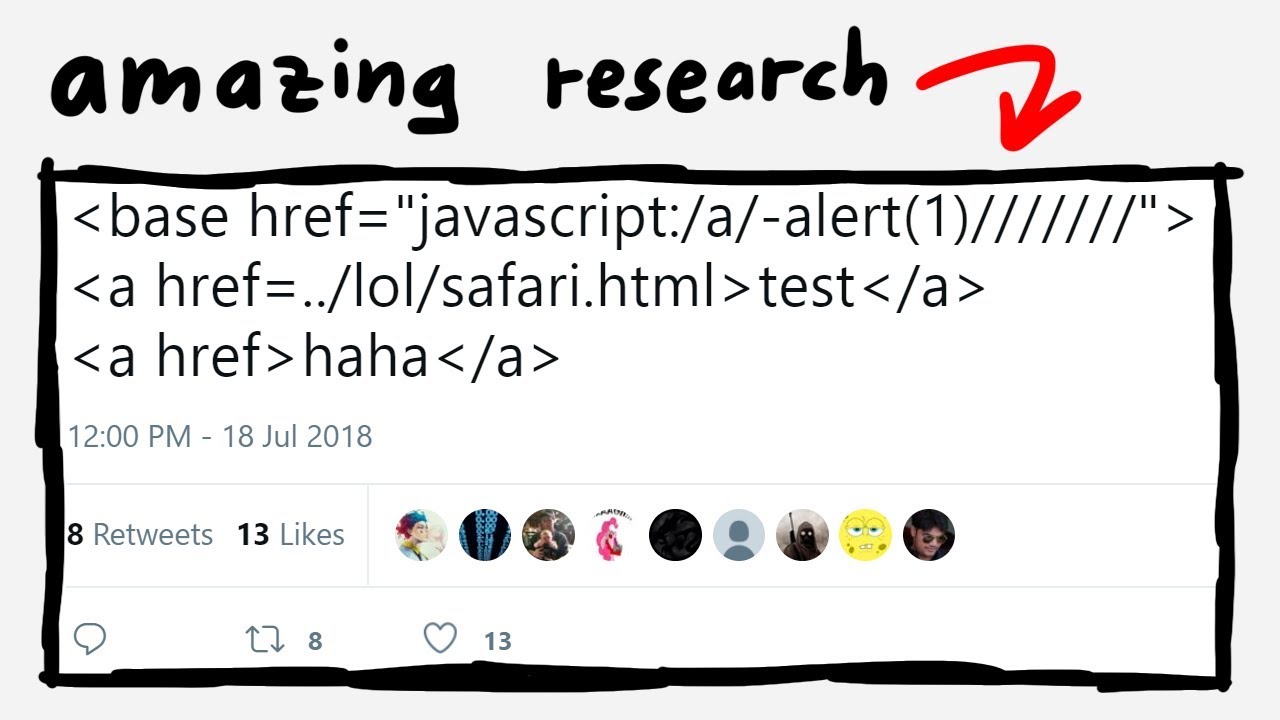
How to get good at XSS? There are a lot of charlatans out their overhyping by posting misleading content. It's infuriating because a lot of the actual research is less flashy and thus more hidden. Maybe I'm a bit too pessimistic in this video, but I think it's a concrete example we can use talk about it.
There are a lot of charlatans out their overhyping by posting misleading content. It's infuriating because a lot of the actual research is less flashy and thus more hidden. Maybe I'm a bit too pessimistic in this video, but I think it's a concrete example we can use talk about it.
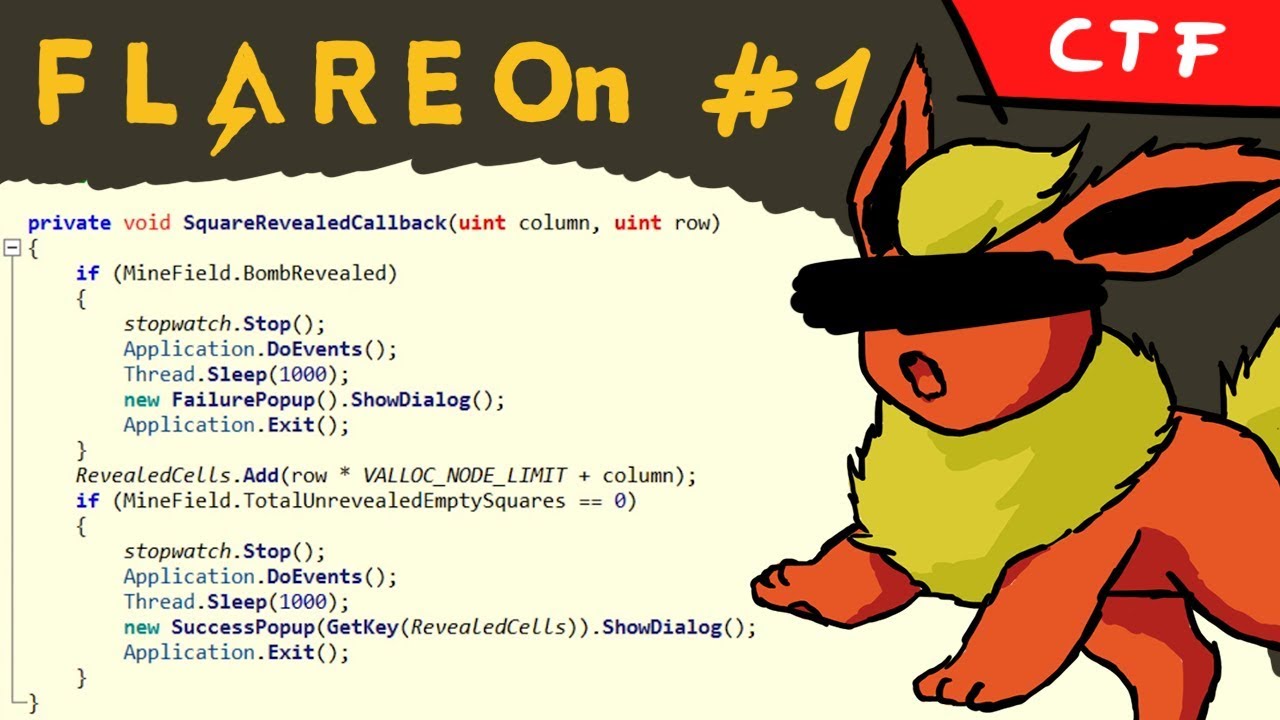
This challenge was part of the FLARE-On 2018 CTF. In this video we reverse engineer a basic windows .exe to find out how to win the game. At first we tried to attack the weak crypto but failed. At the end it turns out I had a bug in my code :(
This challenge was part of the FLARE-On 2018 CTF. In this video we reverse engineer a basic windows .exe to find out how to win the game. At first we tried to attack the weak crypto but failed. At the end it turns out I had a bug in my code :(
In this video we figure out how to do a popunder in Chrome version 59, by using a trick.
Reversing obfuscated JavaScript of a pop-under technique for Google Chrome version 60 on Windows.
Reversing obfuscated JavaScript of a pop-under technique for Google Chrome version 60 on Windows.
Video write-up about the Real World CTF challenge "flaglab" that involved exploiting a gitlab 1day. Actually two CVEs are combined to achieve full remote code execution.
Using a SSRF to target Redis in a GitLab exploit, in order to achieve remote code execution.